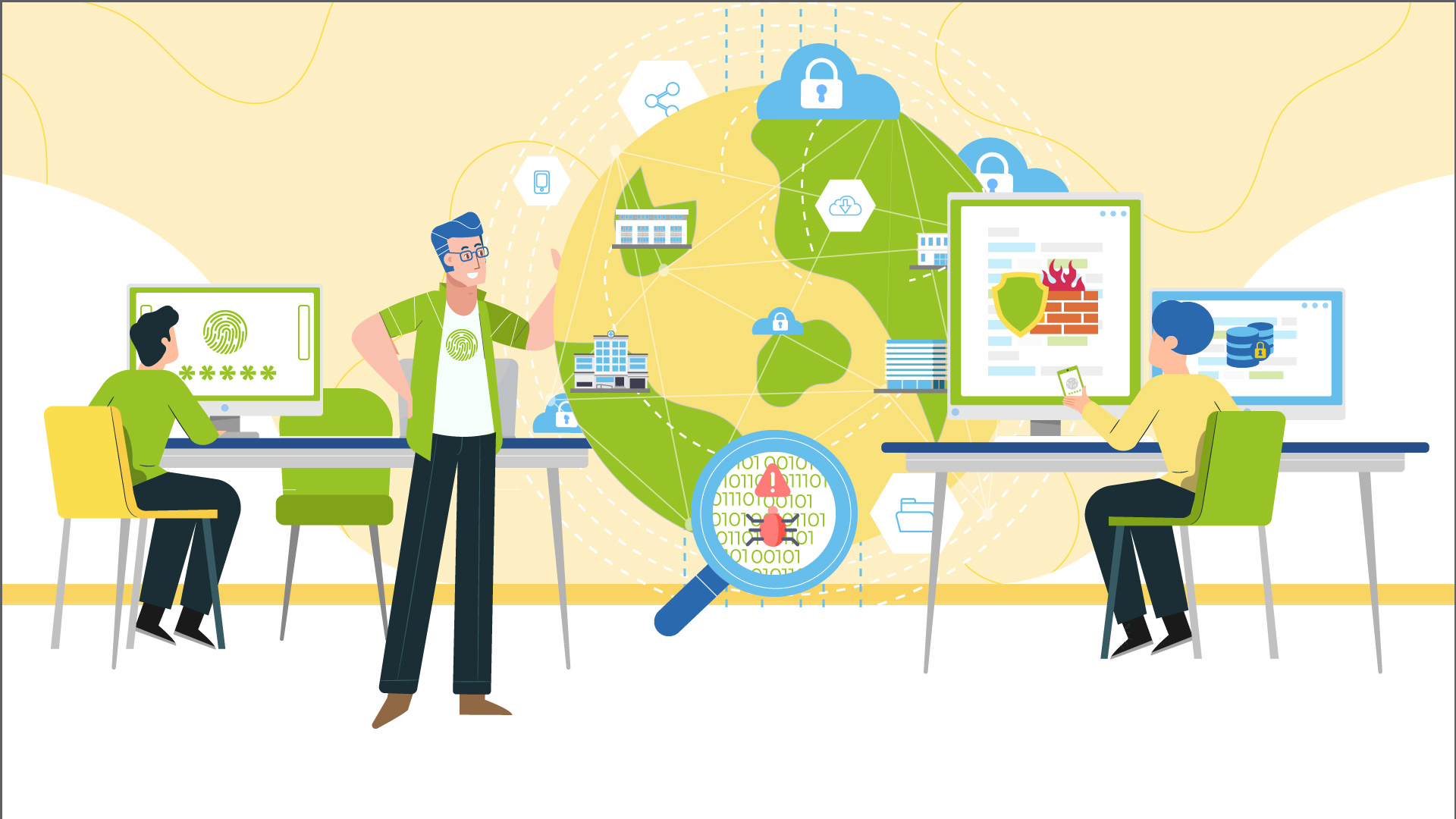
Cyber attacks are inevitable
…but the extent of their impact depends on your security measures. Methodologies and standards that distill best practices into structured guidelines help you make a risk based security strategy and allow you to gradually grow your security maturity over time.
Is your company NIS2 ready?
Investing in good cyber security pays off, especially in view of the integration of the NIS2 Directive. By 17 October 2024, all EU member states must transpose the NIS2 Directive into national legislation, after which the requirements will become effectively enforceable.
What does it mean for your organisation? How do you best tackle this? Axians helps your company prepare for the NIS2 Directive.
The 3 types of security
How high-level is your security?
Just like crumple zones and seatbelts in cars, your systems need passive measures as a base for the rest. Segmentation, visibility in who and what devices are on the network and what connects to the internet, a back-up, a business continuity plan,… Measures that will not avoid a security breach but will help you contain it and limit the extent of the problem.


In the ‘active‘ stage of safety, the measures are not merely responding to threats when they happen, but have a more active role in preventing them.
In this stage we find Firewalls, IDS/IPS (intrusion detection/prevention), Network Access Control/NAC, content filtering sandboxing, identity and access management, vulnerability management,…

The next stage can be compared to driver assistance or automated driving for cars. It contains autonomous/SelfDriving features, like behaviour analyses, anomaly detection, orchestration and automation,…
You can’t control what you don’t know exists. Network flow monitoring and security Incident and event management will give you the insights you need to detect, prevent, contain and respond to threats.
Build a security mindset
Security is a mindset, consisting of four main activities. Axians helps you strengthen all four of them, for consistent protection.

Security in the OT world
OT environment: passive or active security?
In an Operational Technology (OT) environment, passive security is usually the better option. Often, the use of sensitive older infrastructure makes security incidents more difficult to pinpoint: for example, if a motor starts rotating at a higher speed than usual, it is harder to know whether this is due to a security problem or for another, technological reason. A common factor across all types of devices is that they are part of the network and all talk in terms of TCP/IP. Monitoring network traffic flows can therefore be of great value.
Full visibility
Know what is happening on your network! End-to-end visibility with rich details and real-time flow monitoring gives you detailed insight.
Identity services
Know who is connected to your network, both locally and remotely. Identity is often not present in industrial environments: machines are not domain joined, have local user access and administrator rights, no central management, so passwords are often not changed. An IP alone is not an identity because it is very easy to spoof.
Network segmentation
Should an incident or attack happen, how can you isolate the impact? How can you keep it from spreading further? Reduce the attack surface and minimize potential impact. Isolate logical entities into separate network segments to stay in control over data flows.
Configuration standardization
Environments can start securely, but how do you know certain restrictions have not been removed? Policy-verified configuration mitigates human errors. Complex configurations can be verified automatically for compliancy.
Case study
Learn more about our customers’ stories
-
Oiltanking: improving OT security
Oiltanking is one of the largest independent operators of tank terminals for oils, chemicals and gases worldwide. They asked for a network security assessment in order to understand their exposure to a potential cyber event. We helped them get a precise view of their existing ICS infrastructure and a clear understanding of the cyber risks they were facing.Read more
Cybersecurity at VINCI Energies: SOC customer case

Axians: the best of ICT with a human touch

Why work with Axians?
Axians stands for reliability and unburdening. Our mission is ICT with a human touch, meaning we are easily approachable for our clients and give their business individual attention – we speak your language. Come to us if you want to co-create a solution that is tailor made for your business, using strong, standardized building blocks and a proven methodology. After all, we like to think with you long term. You’ll find us in your close proximity, and at the same time you’ll benefit from our large Axians global network.